With the ever-evolving landscape of cloud, industries and cloud service providers are making significant moves. However, despite this progress, the paramount concern remains securing sensitive data. To effectively safeguard sensitive information, it is crucial for stakeholders to familiarize themselves with best practices for cloud security. These practices encompass protecting data, ensuring secure information processing, and implementing technical measures within the realm of cloud computing. The primary goal is to shield this data against unauthorized access, whether during its transit over the internet, and to prevent accidental or unlawful tampering, data loss, or theft.
Table of Contents
ToggleCloud and Modern Industries
The recent adoption of cloud computing technology has opened up exciting opportunities for businesses across the globe. It has not only benefited cloud service providers but has also created a growing need for effective cloud security measures.
Cloud security entails a comprehensive approach, combining people, processes, and technology with defined policies to safeguard data and applications. Businesses must ensure the protection of their sensitive data to prevent potential damage to their reputation, as a security breach could have catastrophic consequences.
This article delves into the evolving landscape of cloud security and outlines the challenges faced by different industries in ensuring the safety of their data. It also provides insights into best practices that businesses should adopt to navigate this complex terrain successfully.
Cloud & Key Cloud Security Concerns
As companies are embracing cloud computing, they entrust cloud service providers (CSPs) with the responsibility of maintaining a secure environment for their data and applications. However, if CSPs do not adequately manage IT and cybersecurity parameters at every layer, security risks can arise. The concentration of valuable data within a single location makes CSPs attractive targets for malicious activities. To mitigate these risks, CSPs need to ensure that essential security practices are adopted for better cloud security.
Key Cloud Concerns
Several cloud security concerns must be addressed to protect government data effectively. These concerns include:
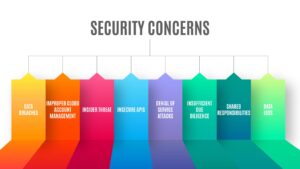
Data Breaches: Although cloud computing enhances security measures, it does not guarantee immunity to data breaches. Industries leveraging the cloud must ensure that reliable and robust security policies are enforced to prevent data breaches.
Improper Cloud Account Management: The development of cloud services has introduced new challenges in managing user accounts. Appropriate account management methods are essential to protect against unauthorized access and data manipulation.
Insider Threat: Insiders within any respective industry may misuse their authorized access to cloud services to access sensitive information. Implementing access control mechanisms is vital to mitigate this risk and bring a pause to these insider threats.
Insecure APIs: Application Programming Interfaces (APIs) provide opportunities to customize cloud platforms. This also introduces several security vulnerabilities. Reliable and effective encryption, authentication, and access control are essential to bring security to sensitive data.
Denial of Service Attacks: Denial-of-service attacks aim to disrupt services and servers, making them unavailable to legitimate users. It will help in employing countermeasures to mitigate these disruptive attacks effectively.
Insufficient Due Diligence: Thorough due diligence in managing internal cloud controls is essential. Neglecting to oversee user-level cloud configurations can introduce substantial security vulnerabilities.
Shared Responsibilities: Cloud security necessitates collaboration between the CSP and the cloud consumer. Neglecting or omitting the user’s role in security responsibilities can jeopardize the integrity of data.
Data Loss: Data on cloud platforms can be lost due to various factors, including natural disasters, data deletion, or malicious attacks. A comprehensive recovery plan is essential to mitigate the impact of data loss.
To address these challenges, different industries either directly or through System Integrators (SIs) and Managed Service Providers (MSPs), must collaborate closely with CSPs to secure their critical data effectively.
Best Practices for Cloud Security in the Industry
Migrating to the cloud is a significant step for any industry in this era. Moreover, it’s also crucial to establish robust security measures at various levels to ensure a secure transition to the cloud. This section focuses on industry-specific best practices for cloud security, emphasizing the need for secure cloud adoption.
A Layered Approach to Security
Cloud security should be approached in a layered manner, spanning from the physical infrastructure to data, applications, and user access. This layered approach ensures comprehensive protection. In the industry context, this approach is critical for safeguarding sensitive business information.

Data Security
Ensuring the security of data in the cloud is of utmost importance. Industry players must implement data protection measures similar to those used in traditional data centers. Key data protection practices include:
Encryption: Utilize encryption to safeguard data both during transmission and while at rest. Multiple encryption methods, such as Full Disk Encryption (FDE), Format Preserving Encryption (FPE), and more, should be considered. It should be encrypted before moving it to the cloud or during transfer using secure connections (HTTPS, SSL, TLS, FTPS).
Data Classification: Categorize data based on sensitivity (Restricted, Confidential, Sensitive, Unclassified) to apply appropriate security measures.
Data Usage Policy: Establish clear data usage policies, outlining who has access to data and acceptable usage conditions. Moreover, define consequences for policy violations.
Access Control: Implement robust access control mechanisms to manage data access, including administrative and technical controls.
Regular Backups: Conduct regular backups (Full, Incremental, Differential) to ensure data availability and validate recovery procedures.
Data Monitoring: Implement data-level monitoring and ensure logs meet industry compliance requirements.
Application Security
Industry applications hosted in the cloud are vulnerable due to shared resources. Following security measures need to be implemented to safeguard applications:
Micro-service Architectures: Use micro-services to reduce the attack surface of individual virtual machines, enhancing security.
Web Application Security: Protect web applications against various security threats, such as cross-site scripting and SQL injection, using web application firewalls. These defenses are essential for safeguarding sensitive data and content management systems.
Cloud API Security: Implement security tools and authentication mechanisms to protect Cloud APIs from vulnerabilities and attacks.
DevSecOps: Embrace a culture of security integration across all stages of the software development process, addressing security concerns from the outset. It ensures a seamless software development lifecycle.
Multi-tier Application Security: Decide on the appropriate security level for multi-tier applications. Focus on application-level security, which can authenticate and authorize users, with the database trusting the application for access.
Host/Compute
Workloads are the core of cloud computing, encompassing various processing tasks. It is essential to treat virtual machines like physical ones for most activities, bearing in mind that virtual machines are susceptible to data loss, hardware failures, viruses, and security breaches.
Multiple types of computing offerings in the cloud include:
Virtual Machine Manager (Hypervisor): Responsible for abstracting hardware from the operating system, hypervisors enforce isolation and support high-performance operations. Virtual machines are effective security controls, benefiting from ongoing hardware and software improvements.
Containers: These are code execution environments running within an operating system and sharing OS resources. Containers differ from virtual machines as they run distinct processes using the OS’s kernel, making them more efficient and lightweight.
Serverless: This category involves cloud consumers accessing exposed functions without managing underlying hardware or virtual machines.
Workloads from different tenants often share the same physical compute node, necessitating robust segregation capabilities.
Network
In the industrial sector, cloud security extends to virtual networks and data in transit. Virtual networks vary, from basic VLANs to Software-Defined Networks (SDNs), and it’s essential to secure data in transit through network encryption.
Some security measures for network security in industries include:
– Using Virtual Private Networks (SSL or Site to Site) to access cloud infrastructure and services.
– Avoiding disabling personal firewalls on department computers connected to a network.
– Implementing IP whitelisting to allow connections from specific IPs and deny others.
– Pre-certifying additional VLANs, firewall ports, and load balancers.
– Segregating virtual networks and cloud accounts to reduce security risks.
– Restricting traffic between workloads in the same virtual subnet using a firewall policy.
– Minimizing dependency on virtual appliances that may impede elasticity or cause performance bottlenecks.
– Implementing policies and internal security controls to prevent traffic monitoring without approval.
– Registering security scans on new network segments on deployment and adding them to continuous monitoring.
– Configuring automated responses to attacks, including IP blocking, connection termination, and signature analysis.
– Monitoring network traffic logs or implementing a Security Information and Event Management (SIEM) system for real-time security alerts.
– Leveraging SDN capabilities for multiple virtual networks and cloud accounts to enhance network isolation.
Identity and Access
Identity and Access Management (IAM) is crucial for industries, allowing for the definition and management of access privileges for individual network users, both internal and external. In the industrial context, IAM is instrumental in maintaining a secure and seamless access lifecycle for digital identities.
Security measures related to IAM include:
– Implementing Multi-Factor Authentication (MFA) to enhance security and reduce account takeovers.
– Utilizing access control methodologies, such as Role-Based Access Control (RBAC), to manage access to cloud resources by defining what end users can do with allocated resources.
– Assigning appropriate permissions for security teams to gain the necessary visibility into cloud resources.
– Configuring automated responses to detect suspicious actions related to department identities.
– Regularly monitoring user details and access levels to prevent unauthorized access and protect sensitive data.
– Adopting Identity-as-a-Service (IDaaS) for single sign-on.
– Restricting the use of root and generic accounts for cloud management and operations.
– Implementing role-per-group models for access to systems.
– Ensuring resource-level access controls for web, application, and cloud resources.
Perimeter and Physical
Perimeter security and physical security play vital roles in safeguarding industry data and cloud environments. In the industrial sector, it is essential to establish layered defenses to control network traffic entering and exiting data center networks.
To protect data center resources and assets, considerations include:
– Implementing perimeter protection through firewalls and intrusion detection/prevention systems.
– Ensuring that cloud service providers have secure data center facilities with strict physical and perimeter security measures in place.
– Protecting against environmental threats, natural disasters, and other disruptions.
– Safely disposing of or reusing data center equipment.
– Instituting security controls for data center personnel.
– Creating backup, redundancy, and continuity plans for data center operations.
Next-Generation Cloud Security Model: Zero Trust
The concept of ‘zero trust’ emerged in 2010, introduced by an analyst from Forrester Research Inc. In subsequent years, Google’s adoption of zero trust security for their network generated significant interest within the technology sector.
Zero trust security represents a cutting-edge approach to IT security. It mandates rigorous identity verification for both devices and individuals seeking access to resources on a private network, irrespective of their location within or outside the network perimeter. Unlike traditional security models, zero trust doesn’t rely on specific technologies; instead, it embodies a holistic and comprehensive framework that integrates multiple technologies and principles.
Conventional IT network security often follows the ‘castle-and-moat’ paradigm, which assumes that access from outside the network is difficult while inherently trusting everyone inside. However, this approach has limitations. Once an attacker gains entry to the network, they essentially have free rein over all resources within. This vulnerability is exacerbated by the modern practice of dispersing data across multiple cloud service providers, making it challenging to implement a single overarching security control.
Zero trust security, by default, distrusts both internal and external entities, making identity verification mandatory for anyone attempting to access network resources. This additional layer of security is designed to mitigate data breaches.
Businesses can opt for a zero-trust micro-segmentation strategy, allowing traffic to flow between authorized systems and connections, regardless of the network environment.
Adopting Security Standards
For security reasons, it’s essential to tailor information to meet the unique needs of different industries. There are a number of internationally recognized standards that industries can adopt when embracing cloud platforms:
ISO/IEC 27000 Family: Information Security Management System
Within the ISO/IEC 27000 family, several key standards offer valuable guidance for Information Security Management Systems (ISMS) that industries can leverage when navigating the complexities of sensitive data management, policies, and procedures:
– ISO 27001: It outlines best practices for implementing an ISMS, a crucial system for safeguarding sensitive data within organizations. An ISMS is pivotal in defending against cyber-attacks and data breaches, making it an indispensable component for any industry.
– ISO 27002: ISO 27002 focuses on providing guidelines for ISMS practices, encompassing the selection, implementation, and management of security controls that align with an organization’s specific Information Security Risk environment.
– ISO 27017: Tailored to cloud-based organizations, ISO 27017 is designed to aid in the effective implementation of controls. It’s pertinent not only for organizations storing data in the cloud but also for those offering cloud-based services to others, particularly when sensitive information is involved.
– ISO 27018: Specifically aimed at cloud computing organizations, ISO 27018 aims to protect Personally Identifiable Information (PII) that’s stored or processed in the cloud. While primarily relevant to cloud service providers, this standard provides an additional layer of confidence to consumers, especially when collaborating with organizations entrusted with sensitive information.
PCI DSS
Payment Card Industry Data Security Standard (PCI DSS) is a set of comprehensive security requirements applicable to organizations that handle credit and debit card transactions and payment applications. When card payment data is stored, transmitted, or processed in a cloud environment, PCI DSS applies. Compliance necessitates the validation of both the Cloud Service Provider’s (CSP) infrastructure and the client’s usage of the environment. It’s important to emphasize that the shared responsibility between client and provider for managing security controls does not exempt a client from ensuring the proper security of cardholder data as per PCI DSS requirements.
By adhering to these industry-specific security standards, organizations can enhance their data protection efforts and adapt to the unique challenges and regulatory requirements of their respective sectors.
Security in a Multi-Cloud and Hybrid Cloud Environment
Securing a multi-cloud or hybrid IT environment presents a formidable challenge, especially in industries where diverse cloud solutions coexist. Many organizations in these sectors see the hybrid model as a more secure alternative to exclusive in-house systems. Enhanced security plays a pivotal role in encouraging the adoption of multi-cloud or hybrid cloud services. Fortunately, recent changes have transformed the landscape, with cloud service providers (CSPs) now offering enhanced controls and security compliance.
Multi-Cloud and Hybrid Cloud
Multi-cloud refers to using multiple cloud and storage services within a single heterogeneous architecture. This approach distributes cloud assets, software, and applications across various cloud-hosting environments. The essence of multi-cloud architecture is to eliminate dependence on any single CSP, providing flexibility and resilience.
While CSPs are responsible for protecting the cloud infrastructure, it’s the duty of organizations in sectors like finance and healthcare to secure the data they entrust to the cloud. Thus, these organizations must conduct thorough due diligence when selecting CSPs or managed service providers (MSPs) to ensure compliance with relevant regulations and security requirements.
Shifting Security Focus in Multi-Cloud Environments
In multi-cloud environments, the emphasis shifts from securing the network perimeter to safeguarding data at rest and in transit. It’s vital for organizations to understand data flows comprehensively and apply protection commensurate with data sensitivity levels.
Key Considerations for Multi-Cloud Deployment
Here are some measures to keep in mind when planning a multi-cloud deployment:
Centralized Security Strategy: To identify threats across multiple cloud platforms, security teams should centralize security controls. This approach allows for consistent enforcement of security measures across different cloud platforms, ensuring a cohesive security posture. Third-party automation services can aid in scaling cloud security.
Evolving Security Approach: In a constantly evolving threat landscape, security functions must adapt. Monitoring and analyzing threats in real-time is crucial, and continuous upgrades to security measures are necessary to meet evolving security requirements.
Securing Communications: Secure not only data but also the communications governing how applications function. This includes encrypting communications within the control plane, which is often overlooked. Neglecting to secure these control plane communications can create vulnerabilities for malicious exploitation.
Employee Training: Ensure employees follow security protocols and have access only to authorized data and services. Security breaches often occur when unauthorized access takes place, making training and awareness crucial in preventing security incidents.
CASBs, or Cloud Security Gateways, play a vital role in maintaining security controls across multi-cloud deployments. They enable the discovery of internal cloud service usage, monitor user activity on approved services, and offer security alerting.
To maintain security policies consistently across different cloud environments, organizations can utilize centralized policy management solutions. Moreover, a centralized data backup solution ensures data availability, even during disasters. Infrastructure and application logs from different CSP environments can be gathered centrally for security monitoring.
By adopting these practices, industries can securely embrace multi-cloud deployments and leverage the diverse offerings of various CSPs, all while maintaining robust security controls.
Conclusion
Cloud security is a critical consideration for every arena, be it fintech, healthcare, media, and so on since they continue to embrace cloud computing technology. While the cloud offers numerous benefits, it also presents unique challenges related to data security. To effectively navigate this complex landscape, industries whether government or private must work closely with CSPs, implement security best practices, and stay vigilant to safeguard their sensitive information. By understanding the key security concerns and taking proactive measures, businesses can ensure the integrity, confidentiality, and availability of their data in the cloud, protecting their reputation and the trust of their constituents.

